Today Intel is talking about the security features in their upcoming Ice Lake CPUs as a teaser. While SemiAccurate is happy to see any advances in security, those found in Ice don’t catch up to AMD’s 2017 ‘Naples’ Epycs in some key areas much less the newer Rome CPUs.
Today Intel is talking about the security features in their upcoming Ice Lake CPUs as a teaser. While SemiAccurate is happy to see any advances in security, those found in Ice don’t catch up to AMD’s 2017 ‘Naples’ Epycs in some key areas much less the newer Rome CPUs.
There are four main pillars of today’s announcement from Intel, SGX improvements, TME, PFR, and faster instructions. We will take a look at all of these in turn but the biggest news is not a specific technology but a change in attitude. This time around instead of deflecting questions about problems, pointing to lawyers with phone book thick NDAs when asking about documentation, and in general being detached from reality, Intel was open and honest. They answered questions with real answers, correct ones no less, and explained nuances. This may not sound like a big deal to those that haven’t dealt with Intel on this topic in the past, but it is a welcome sea change to SemiAccurate. This bodes well for the future and we hope it continues.
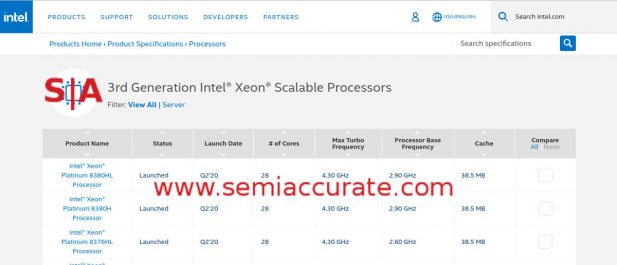
The first (of 3) Intel 3rd Gen Xeon Scalable Processor
Before you celebrate the change, and it should be celebrated, there is another one that is less pleasant. The Ice Lake security briefing talked about the “Intel 3rd Gen Xeon Scalable Processors (codename Ice Lake)”, something we later confirmed was their name. Which is the same name as Intel’s Cascade Lake refresh as you can see from the ARK screen capture above, this link if you want to see for yourself. Ironically this is not the second family to get the 3rd Gen Xeon Scalable Processor title, that honor went to the lamented Cedar Isle 4S Cooper Lake variant when it ‘launched’ a few months ago.
Intel seems so proud of this platform that is isn’t actually on ARK but they did do a song and dance about the launch so it is ‘real’ and available to any customer with the name Facebook and possibly others some day. In any case Cedar Isle is the second 3rd Gen Xeon Scalable Processor, Ice Lake is now the third 3rd Gen Xeon Scalable Processor as you can see from the slide below. Come on Intel, we know marketing is running the company but can’t you at least get some that can count?
The third (of 3) Intel 3rd Gen Xeon Scalable Processor
Getting back to security, the first big announcement is that SGX or Software Guard eXtensions has some major changes. The first big one is that the secure enclave will now cover 1TB of memory and can allow external accelerators to work on secure data. This is good for flexibility, the previous SGX only had a relatively tiny memory space to work in, and should help a lot for people writing SGX code. The down side is that this is somewhat antithetical to the idea of SGX in the first place, basically a small area which only the CPU and certain code bases can access. This change has greatly increased the attack surface of an SGX enclave and the code it contains but SemiAccurate doesn’t know the details of the tech well enough to say whether this tradeoff is worth it, lets just say that it probably is.
Going back to SGX itself, it is a good idea and but has a few problems. The first is that Intel marketing hamstrung adoption by making it optional, aka fusing it off and selling it back on some SKUs, so basically no one used it. The second problem is that you need to recompile your code with special tools to allow it to run in an SGX enclave but realistically you need to rewrite your app from the ground up to use the features that SGX offers. Between it being optional and the effort involved, the only users SemiAccurate could find are governments and a few specialized industries. With luck these new features and widespread availability without a premium will change that.
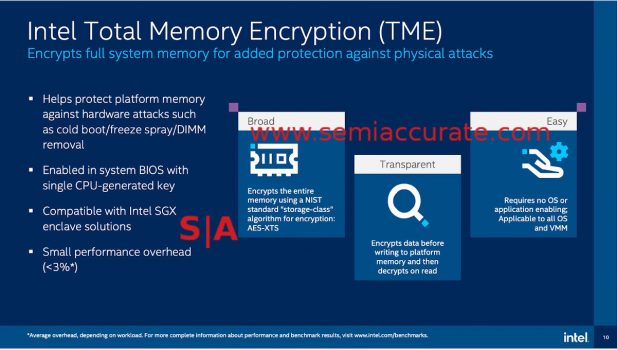
TME does what it says
The next feature is TME or Total Memory Encryption, and it does what it sounds like, transparently encrypts memory. You don’t need to do anything, just turn it on in the BIOS and everything is encrypted. Like AMD’s SME (Secure Memory Encryption) which does the same thing, you take a minor performance hit from enabling TME but this low single digit loss is well worth it if you are at all worried about security.
One glaring feature that is lacking in Ice Lake is MKTME, something that was rumored to be in the platform months ago. MK stands for Multi-Key and it would for example allow you to encrypt each tenant VM in a cloud instance with it’s own key. Since securing cloud users from other cloud users is one of the single most important security use cases, this lack of MKTME is going to hurt Ice’s adoption among the hyperscaler market.
AMD’s SEV (Secure Virtual Machine) tech can encrypt each thread with it’s own key, 510 in Rome, less in Naples, in a transparent way just like TME or SME. SEV also allows you to provision keys to a VM without the underlying host VMM having visibility to the keys, again a critical feature for some large markets, specifically anything with cloud and hyperscaler in the name. All is not lost though, Intel can do some of this with Ice by putting software in an SGX enclave that provisions keys to VMs but it is not hardware, takes coding specific SGX apps for low TAM platforms, and may vulnerable to side channel attacks.
Before you think we are taking a swipe at Intel for SgxPectre. that isn’t the case, attacks and vulnerabilities happen to the best out there, how you deal with them is the differentiator. As we have said previously, Intel used to be awful at this but there appears to be a real change in attitude at the company, they have done pretty well with the last few ‘whoopsies’ that cropped up. That said AMD’s SEV will keep a thread from viewing memory it doesn’t own in hardware, TME and SGX combined can’t and that will be a problem for Ice in some markets.
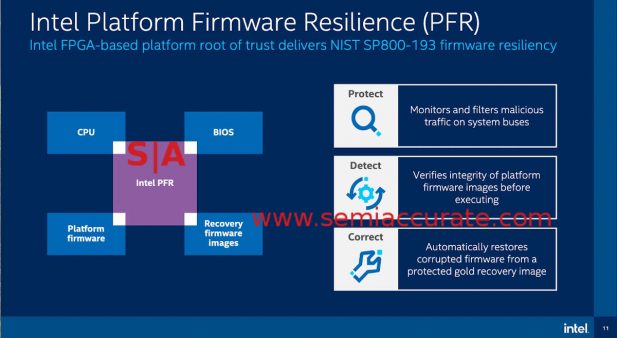
Intel put the FPGA in motherboard with PFR
Probably the most interesting news is PFR or Platform Firmware Resilience, a name for an FPGA sitting on the motherboard that has access to the main system busses. This FPGA, a Max 10 to be specific, can monitor board traffic for unwanted things and act on them. It can also checksum BIOSes and other boot critical platform code for changes and replace them with secure gold masters if tampering is detected. In short this should go a long way to preventing persistent BIOS hacks and similar low level malware.
Intel seems to have done right with PFR even though it is an optional feature on Xeons. While this may limit adoption, PFR really isn’t a user facing technology and it is specific to each board it is placed on. This means coding for the PFR will be the domain of the board vendors and large board vendors at that. Dell, HP, Lenovo and similar companies are the target market, white box makers are unlikely to have the resources to code PFR features and are even less likely to support it over the life of the system. Companies that have their own ILO devices will see an expanded set of capabilities with PFR, the rest will do what they have done in the past. Customers that need the security will specify systems with PFR, the rest probably won’t care. In a perfect world PFR would be on every board with a minimal feature set from Intel but for the first outing, the way it is done will bring tangible benefits to those that want it.
Ice Lake has better crypto instructions
The last major category of improvements is speeding up instructions commonly found in crypto functions. As you can see above VPMADD52 is sped up even if VPMADD1-VPMADD51 are cruelly ignored, AES gets a boost from AVX512, and SHA gets hardware instructions. These are normal incremental improvements in the CPU world but they are welcome nonetheless.
So what do we have today? Intel’s Ice Lake CPUs unquestionably move things forward on the security front. PFR is the most important feature being added today and is somewhat unique in the space, SemiAccurate isn’t aware of an equivalent from a platform vendor. TME is also a welcome addition but given the lack of an equivalent to AMD’s SEV, anyone needing real memory encryption will deploy Epyc.
SGX’s changes likely are a good thing but marketing may have doomed that tech years ago. Even if clever coders can mostly match SEV’s secure key deployment capabilities, they can’t match the side channel protections. That said the added cost of rewriting apps from the ground up make SGX the domain of the few niches that need extreme security but not multi-key memory encryption. So in a nutshell, Ice’s advances are good and welcome but don’t catch up with AMD’s 2017 Epyc CPUs on most grounds while exceeding it in a few. The only absolute is that this time around, buyers are much more aware of hardware security features and are starting to spend based on them.S|A
Charlie Demerjian
Latest posts by Charlie Demerjian (see all)
- Intel Announces their NXE: 5000 High NA EUV Tool - Apr 18, 2024
- AMD outs MI300 plans… sort of - Apr 11, 2024
- Qualcomm is planning a lot of Nuvia/X-Elite announcements - Mar 25, 2024
- Why is there an Altera FPGA on QTS Birch Stream boards? - Mar 12, 2024
- Doogee (Almost) makes the phone we always wanted - Mar 11, 2024