![]() At Techcon this year Rambus was showing off a few new sideband countermeasures, a core and some libraries. If you want to have sideband-proof crypto in your next device but don’t want to do it all yourself, these products are for you.
At Techcon this year Rambus was showing off a few new sideband countermeasures, a core and some libraries. If you want to have sideband-proof crypto in your next device but don’t want to do it all yourself, these products are for you.
SemiAccurate told you about the Cryptography Research arm of Rambus a while ago and they haven’t been sitting still. Their main product has been IP on how to implement sideband attacks on crypto infrastructure, mainly techniques and education. If you are rolling your own device or core and care about security, this kind of thing is mandatory.
The two new parts start with some libraries that run common crypto algorithms in a way that prevents sideband attacks from succeeding or at least makes them much harder to carry out. Obviously Rambus would not tell us exactly how it works but it doesn’t take a genius to have a few clues on how to do it. You could run the same algorithm with hundreds of keys only one of which is real, you could run inverses of the keys after the first pass, or may other similar things. In short you add noise to the leaked information to obscure the key.

The demo hardware running on FPGAs
On the core side things are a bit more interesting. You can get a Rambus/Cryptography Research core as either a crypto accelerator for ARM based system or to implement on FPGAs. There is one of the cores implemented in the above demo and another without the protection running the normal crypto routines. Rambus was sniffing both to show off what their IP was capable of doing.
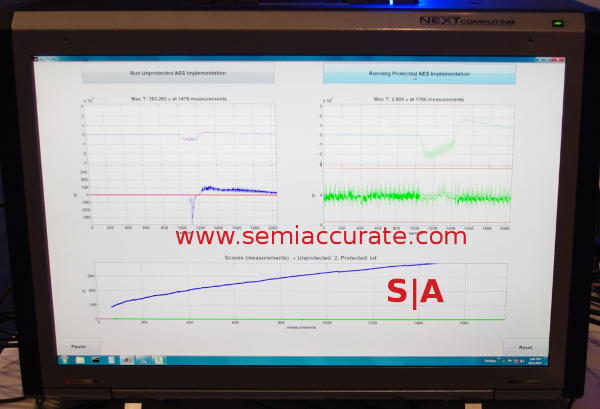
Protected and not protected, then together
The picture above shows what happens when you sniff the two cores for EMI leakage but the same techniques also work for power, heat, and other types of attacks. On the left and right you have unprotected and protected cores respectively, the bottom shows some totals. The top bar roughly shows activity on the cores with the non-linear bit being where the crypto algorithm is running. The bottom line is the radiation on the frequency the snooper is interested in.
As you can see the open core is quiet until the crypto algorithm is run, the protected core is noisy all the time. You can tell when there is crypto work being done and when it is not, the protection makes this much harder to spot. Please note that the ‘attackers’ in this case knew what to look for and when, picking the protected activity out without knowing the precise frequencies would be much harder.
The bottom graph shows roughly the cumulative deviation from random or expected noise, IE the total non-random information. This is a good proxy for information ‘leaked’ that can be used to craft a sideband attack. While the protected core does increase, it increases at a vastly lower rate than the unprotected core. In short the core ‘works’ in that it doesn’t leak nearly as much info for an attacker to use against your cores.
That is about it, cores and libraries that are sideband crypto attack resistant. They both work by minimizing the leaks of data through sideband channels to obscure the interesting bits. We mean bits literally by the way but the pun was intended too. If these cores and libraries can reduce information leaked by a few orders of magnitude, it will harden the cores against attacks by similar margins or more.S|A
Charlie Demerjian
Latest posts by Charlie Demerjian (see all)
- ARM ‘cancels’ Qualcomm’s IP license - Oct 23, 2024
- Microsoft Hobbles Intel Once Again - Sep 20, 2024
- What is really going on with Intel’s 18a process? - Sep 9, 2024
- Industry pioneer Mike Magee has passed away - Aug 12, 2024
- What is Qualcomm launching at IFA this year? - Aug 9, 2024